Article 2 of series Sophisticated Anti-Forensics Tactics and How to Spot Them: Timestomping
Timestomping is widely used by threat actors simply because it is easy and accessible, even for the most novice user. A tool called NewFileTime illustrates this point well. NewFileTime is a free timestamp manipulation tool for Windows that comes with an easy-to-use graphical user interface (GUI) to manipulate timestamps (Figure 1). It offers many straightforward capabilities, such as modifying timestamps of several files and/or folders at once, changing the file timestamps to be younger or older, setting timestamps of a file to any desired time and setting timestamps to a file where the timestamp is in the file name. While NewFileTime isn’t the only program capable of timestomping, the general concept can apply to other tools.
Figure 1 – NewFileTime graphical user interface (GUI) at launch
Files can be added to NewFileTime by dragging and dropping them to the white canvas (Figure 2).
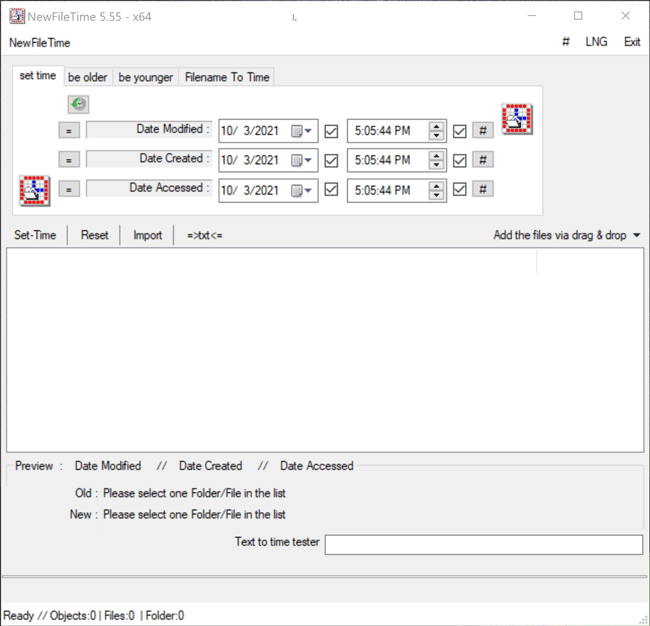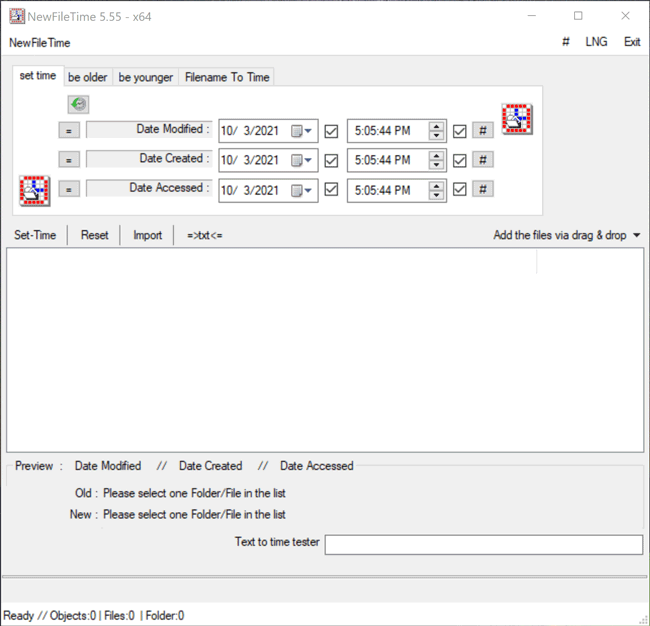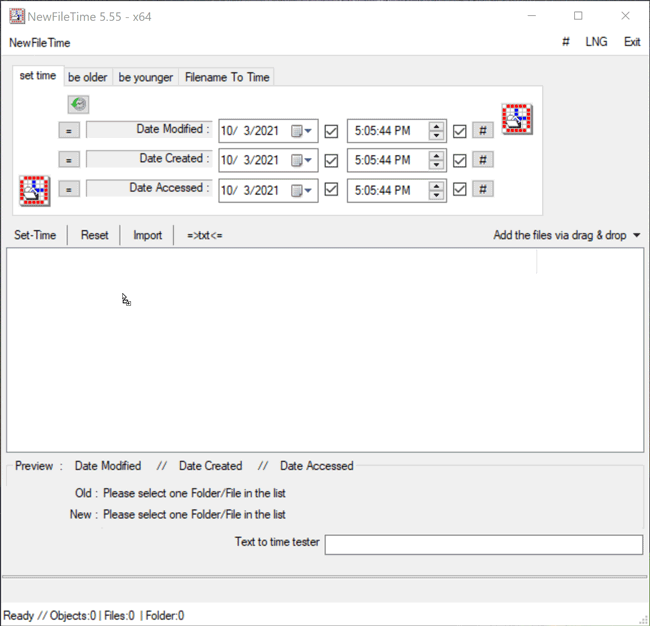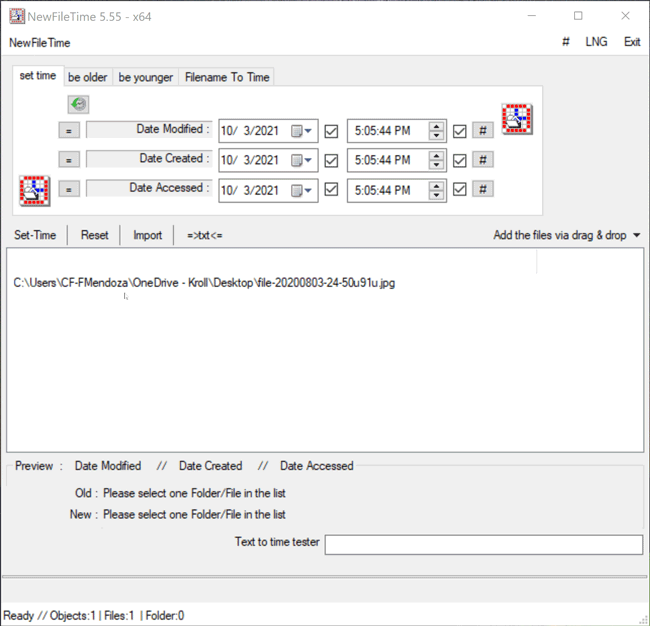
Figure 2 – Dragging and dropping the desired file into NewFileTime
Once the file is selected, the proposed timestamp changes will appear on the bottom (Figure 3).
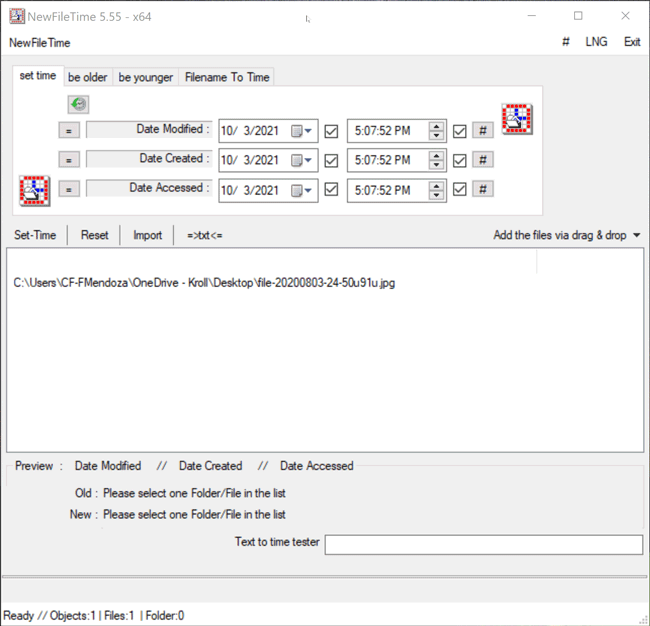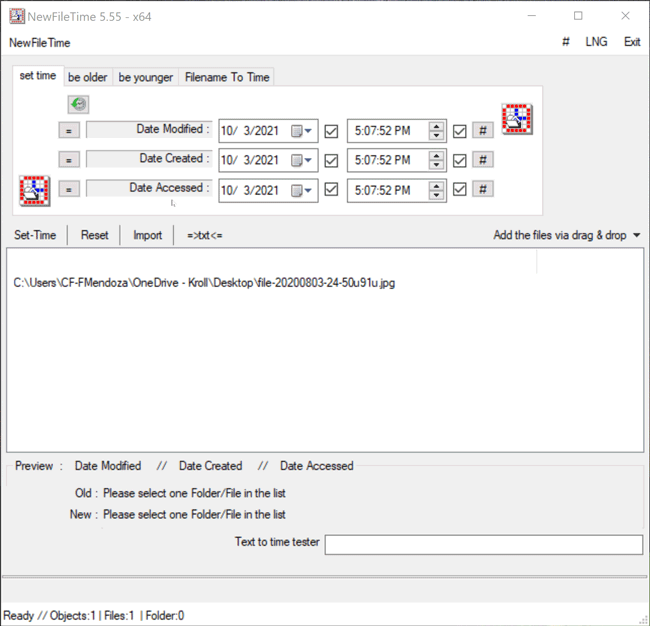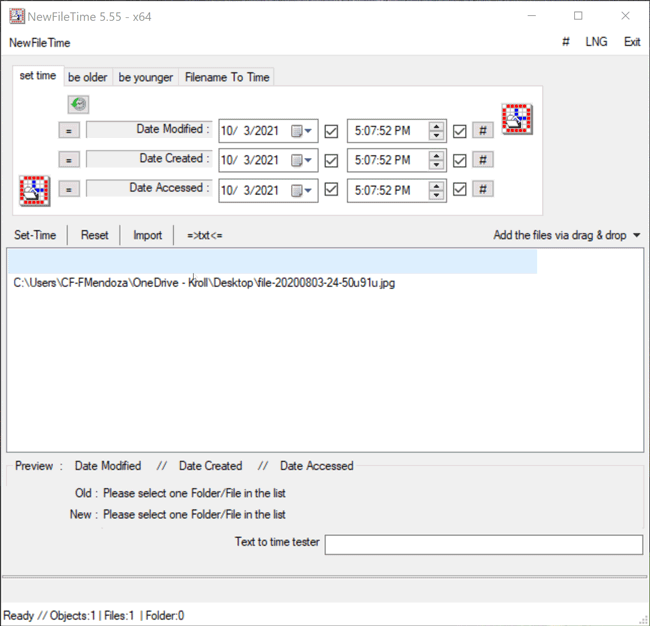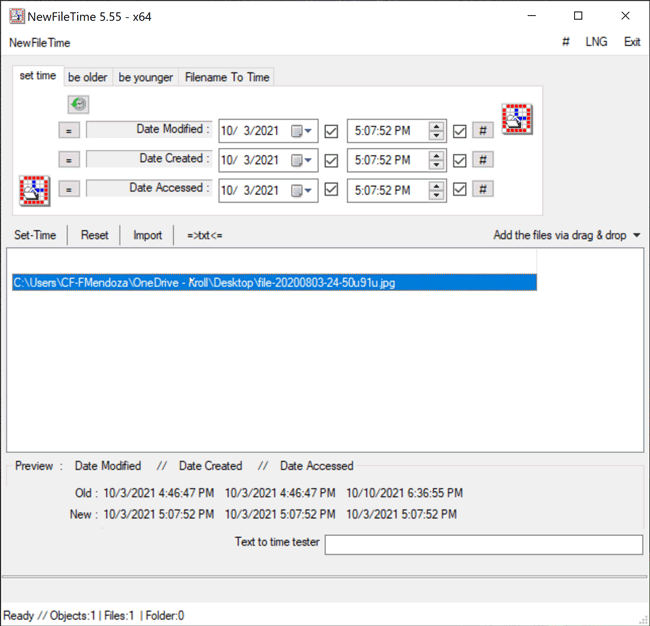
Figure 3 – Hovering over file in NewFileTime to view timestamps
Timestomping Methods with NewFileTime
NewFileTime provides multiple methods of timestomping: Set Time, Be Older, Be Younger and Filename to Time.
Set Time
The Set Time feature in NewFileTime allows a user to set the timestamps for Date Modified, Date Created and/or Date Accessed. On the “set time” tab of the tool, the user can select the dropdown next to the date to select the new date for each timestamp. Once that is complete, the user can then select the hashtag (#)button to set a time at the top of the hour for each timestamp and then click on one of the checkboxes to update the timestamps. The Set Time button will then allow the file to adopt the new timestamps (Figure 4).
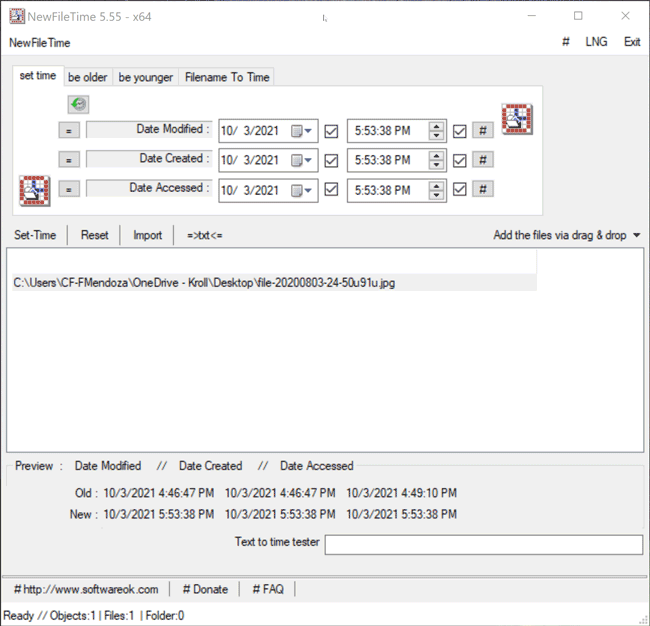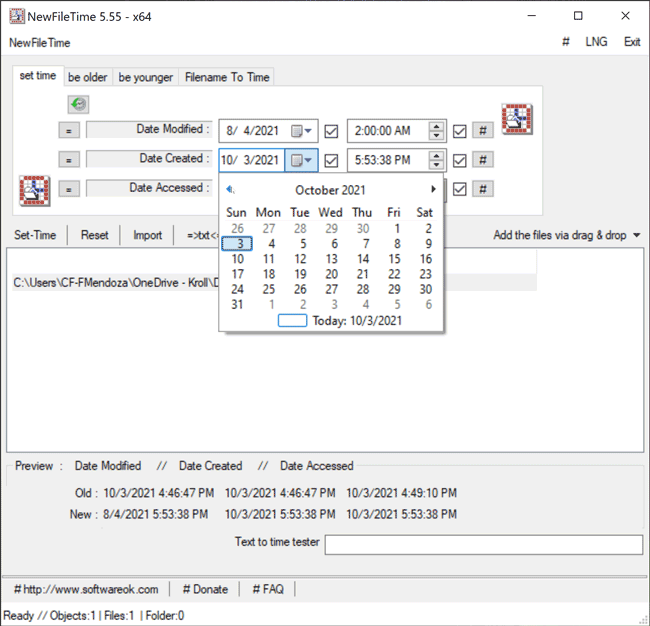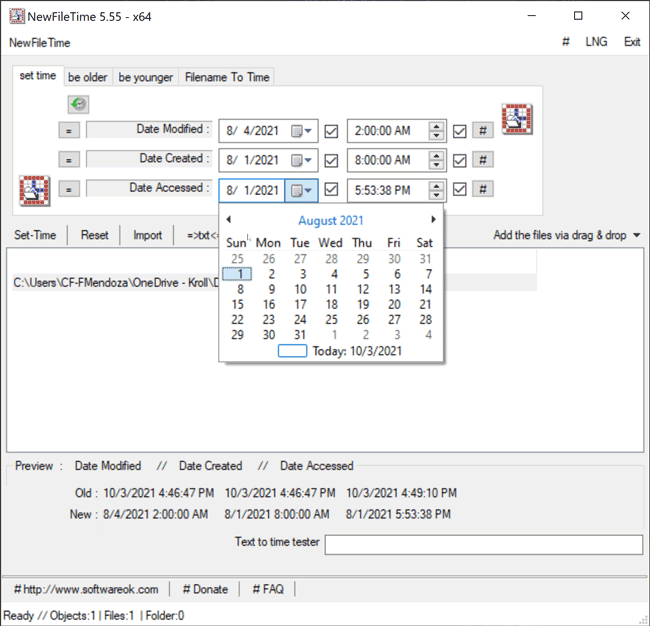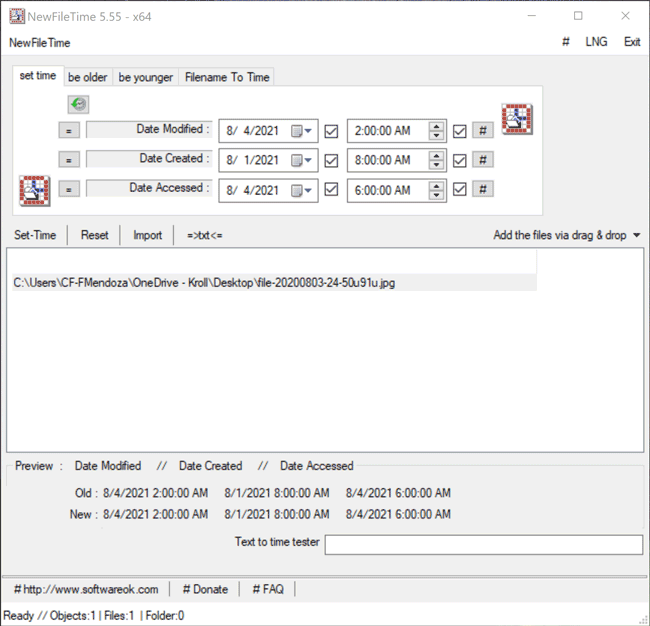
Figure 4 – Set Time feature in NewFileTime
Be Older
The Be Older feature in NewFileTime allows a user to set the timestamps for Date Modified, Date Created and/or Date Accessed to an older date/time. On the “be older” tab of the tool, the user can enter the number of days they want each timestamp to be older than the original date/time. The user can select the hashtag (#) button to set a time at the top of the hour and then click on one of the checkboxes to update those times. Once that is complete, the Set Time button will allow the file to adopt the new timestamps (Figure 5).
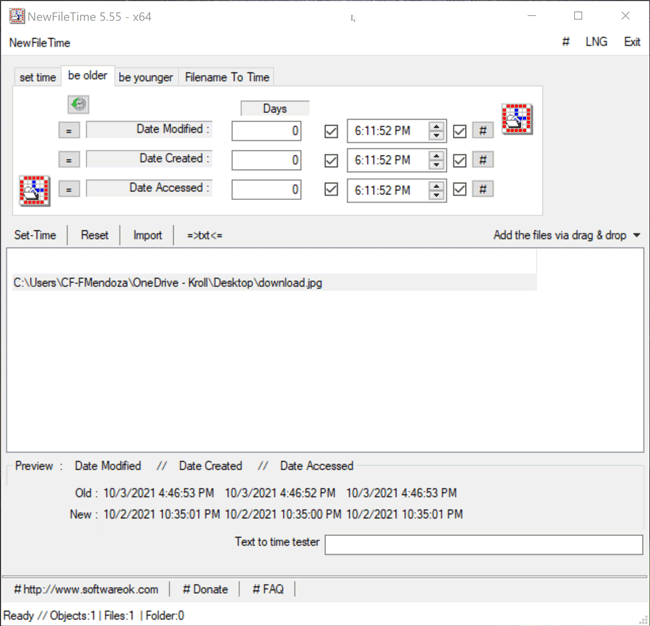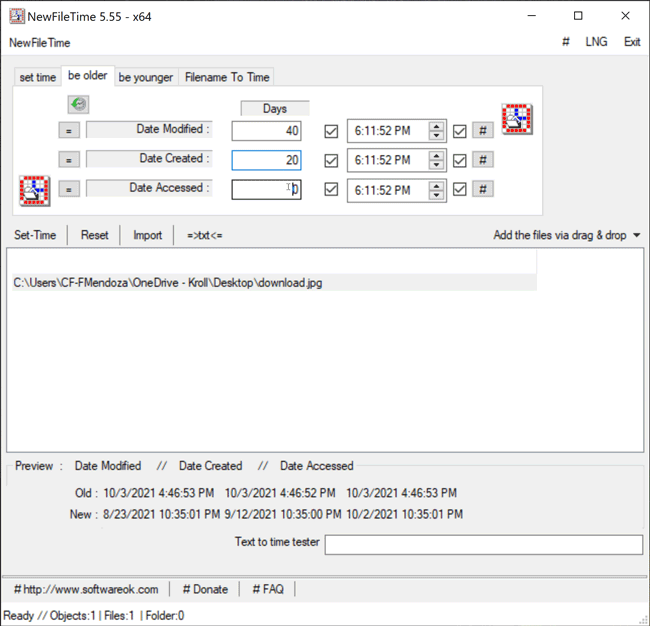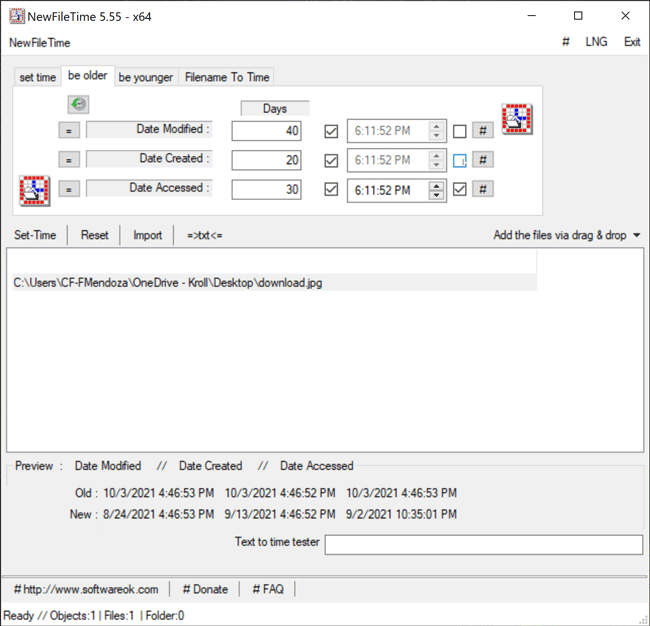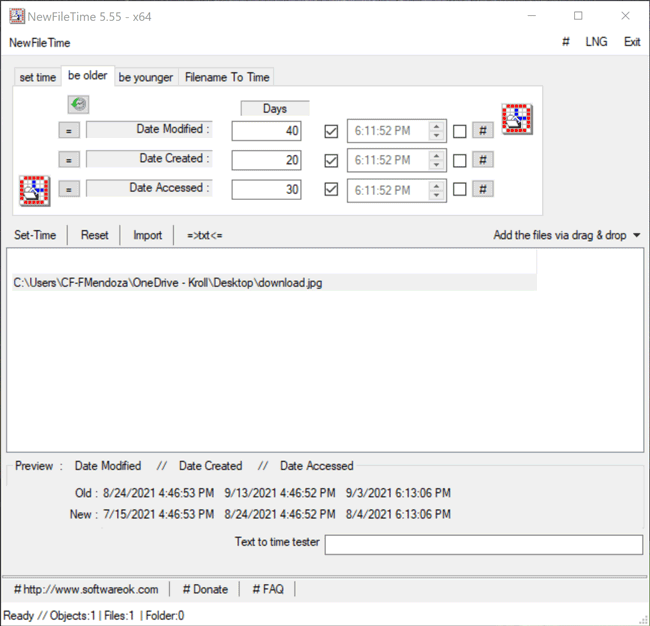
Figure 5 – Be Older feature in NewFileTime
Be Younger
The Be Younger feature in NewFileTime allows a user to set the timestamps for Date Modified, Date Created and/or Date Accessed to a more recent date/time. On the “be younger” tab of the tool, the user can enter the number of days they want each timestamp to be younger than the original date/time. As stated previously, the user can select the hashtag (#) button to set a time at the top of the hour, and then click on one of the checkboxes to update those times. Once that is complete, the Set Time button will allow the file to adopt the new timestamps (Figure 6).
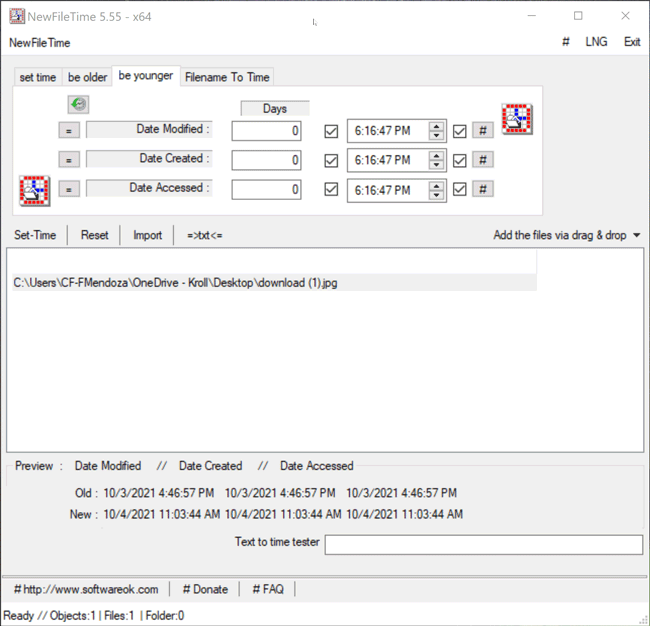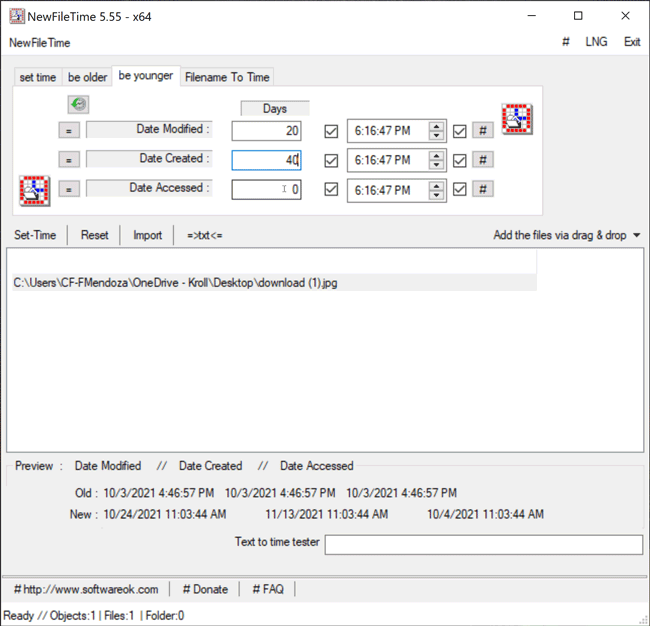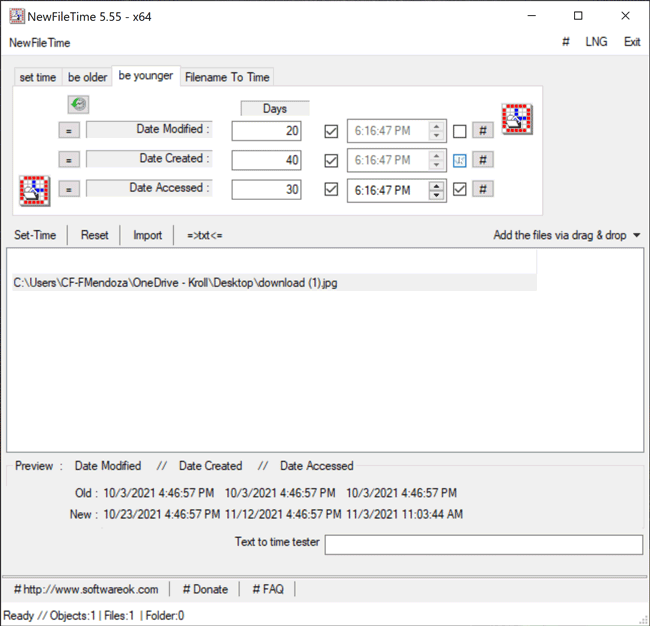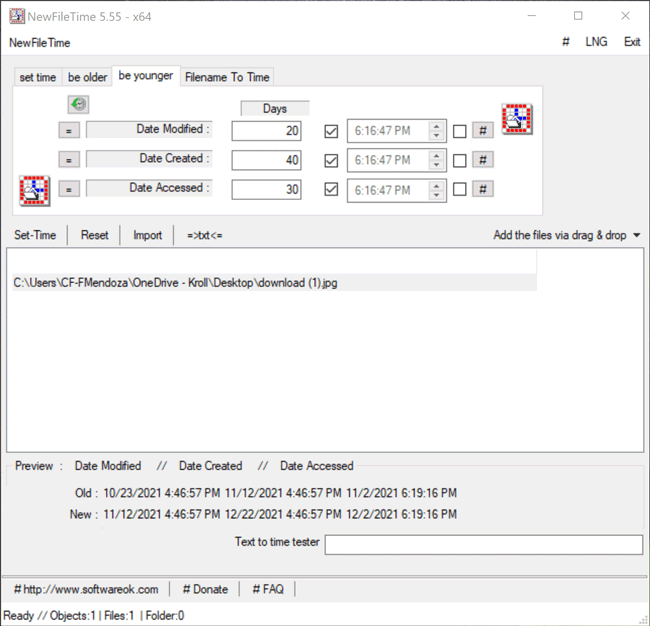
Figure 6 – Be Younger feature in NewFileTime
Filename to Time
The Filename to Time feature in NewFileTime differs from previous methods demonstrated as it allows a user to change the timestamps for Date Modified, Date Created and/or Date Accessed for multiple files at once by inheriting the timestamp of the filename if the timestamp is in the following format: YYYY-MM-DD HH.MM.SS or YYYY-MM-DD_HH.MM.SS. For example, a file named “cat-toes-paw-number-paws-tiger-tabby_2021-10-26_15.00.00” will adopt the new timestamp of 2021-10-26 15.00.00 for Date Modified, Date Created and/or Date Accessed, depending on which timestamp the user chooses to change. The user simply needs to drag the files over to the white canvas in NewFileTime. Once that is complete, the user can uncheck any of the Date or Time checkboxes where they do not want to change the timestamp for Date Modified, Date Created or Date Accessed. If all three timestamps are to be changed, then leave all checkboxes checked as this is the default option. Once that determination is made, the Set Time button will allow the files to adopt the new timestamps all at once (Figure 7).
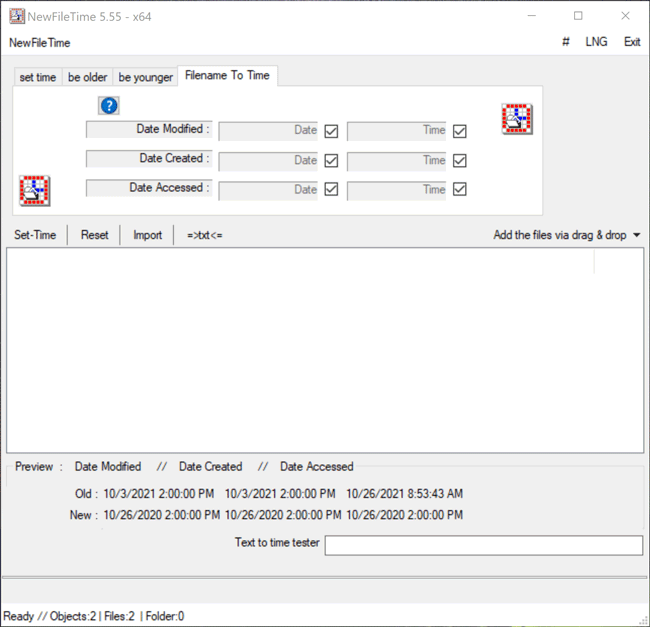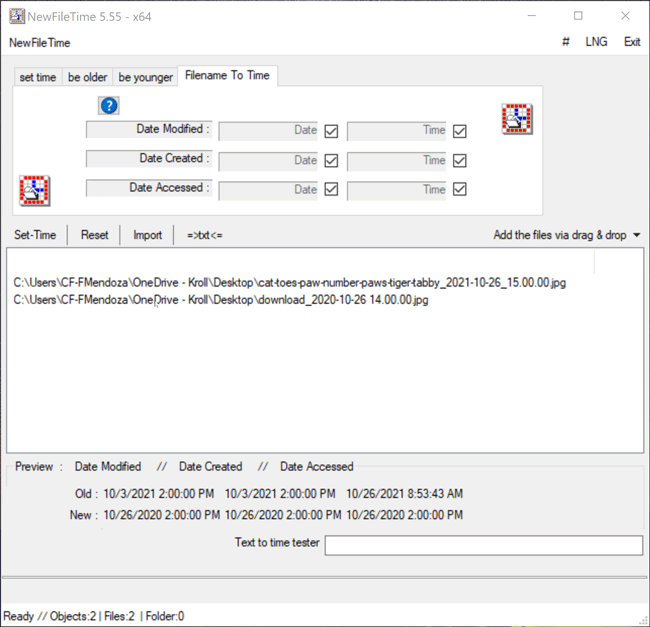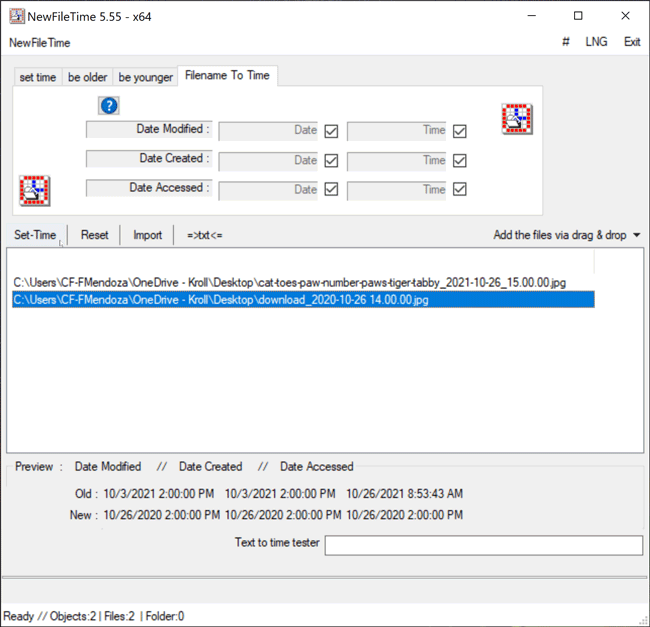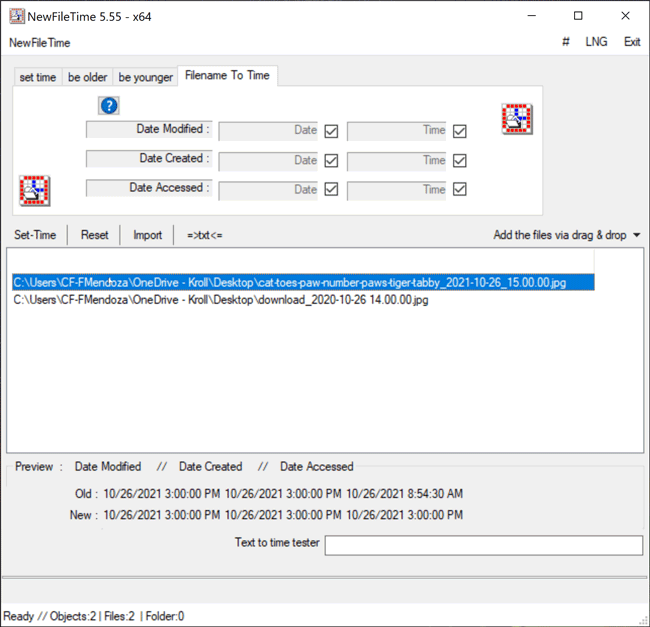
Figure 7 – Filename to Time feature in NewFileTime
As demonstrated, NewFileTime provides users with the capability to easily timestomp files in different ways. Since a timestomping tool such as NewFileTime is free and so easy to use, threat actors commonly take advantage of timestomping to further enhance their ability to hide any malicious activity on a system.
Looking Ahead
In the next article, we will demonstrate how to observe timestomped data using tools such as KAPE and Timeline Explorer.
Related Articles







